VIPER

VIPER is a tool I developed to enhance the capabilities of the Wazuh Unified SIEM XDR. Its primary objective is to enrich alerts generated by Wazuh using external data sources and produce AI-generated summaries. These summaries are designed to be clear and concise, ensuring that even non-technical users with minimal experience can understand and act on them effectively.
VIPER is fully open source. You can find source code on GitHub,

How Does it work?
VIPER enriches alerts by leveraging external data sources. Currently, it integrates with VirusTotal and AlienVault OTX, with a long-term vision of supporting as many threat intelligence platforms as possible.
But does that mean you'll need to spend a fortune on API keys to use VIPER?
No. VIPER is designed with flexibility in mind. If you choose not to use a specific service or its API, you can simply omit it from the script. VIPER is fully compatible with the free API offerings of VirusTotal and AlienVault OTX, ensuring it remains cost-effective while still delivering enriched threat insights.
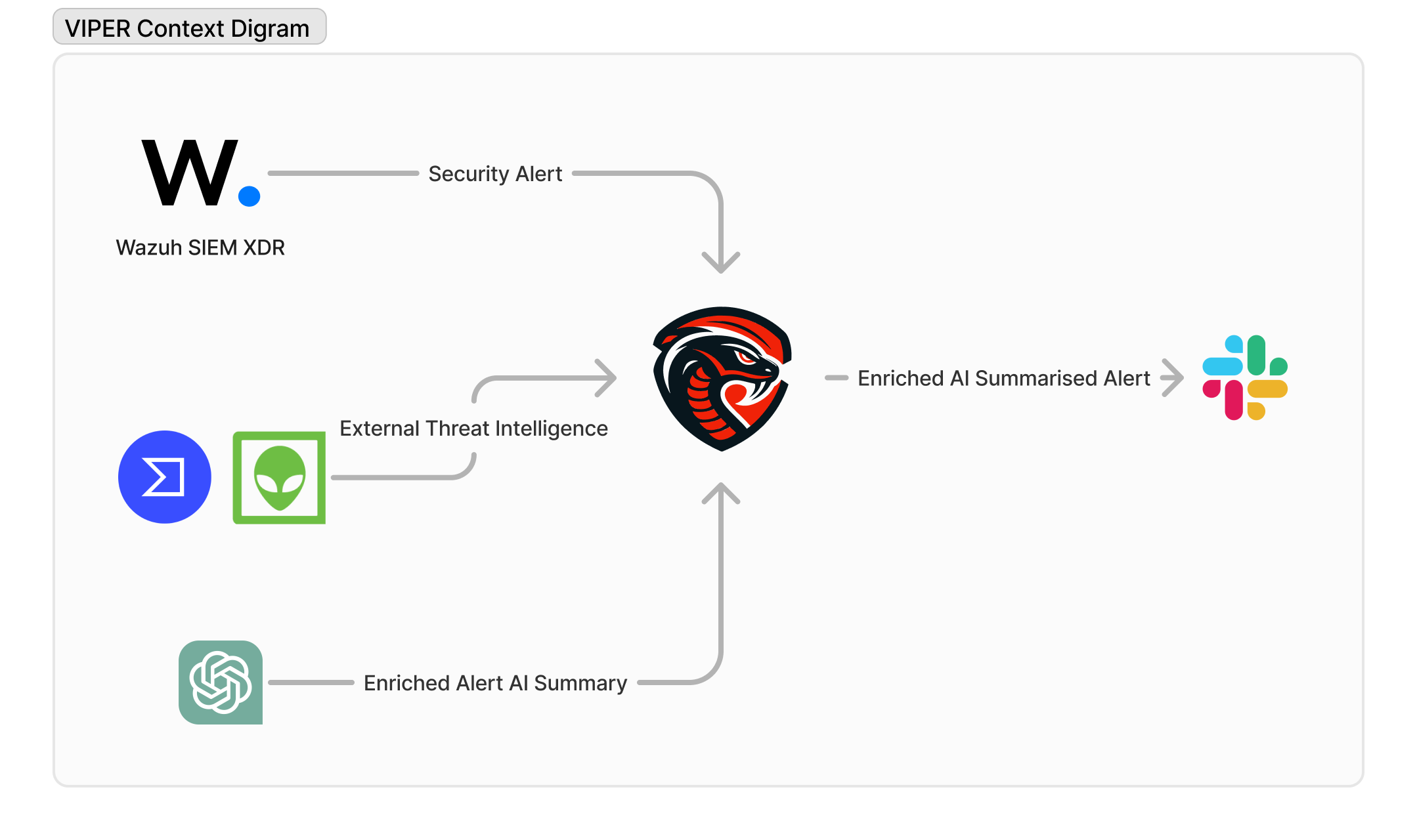
VIPER receives alert data from Wazuh whenever an alert is triggered. It identifies the type of alert generated—such as File Integrity Monitoring (FIM), IP-based alerts, and more. Based on the alert type, VIPER extracts relevant details like file hashes or IP addresses and queries external threat intelligence platforms for additional context. After gathering and filtering the information to remove unnecessary details, VIPER forwards the refined data and parts of the alert to ChatGPT via the OpenAI API. The AI then generates a concise, actionable summary tailored for security teams.
The AI can be customised to meet your specific needs by modifying the system message sent before the gathered threat intelligence details. Once the AI generates a summarised response, it is combined with additional simplified details and formatted into a clear and concise Slack message. This message is then sent to the specified Slack channel, ensuring timely and actionable insights for your team.
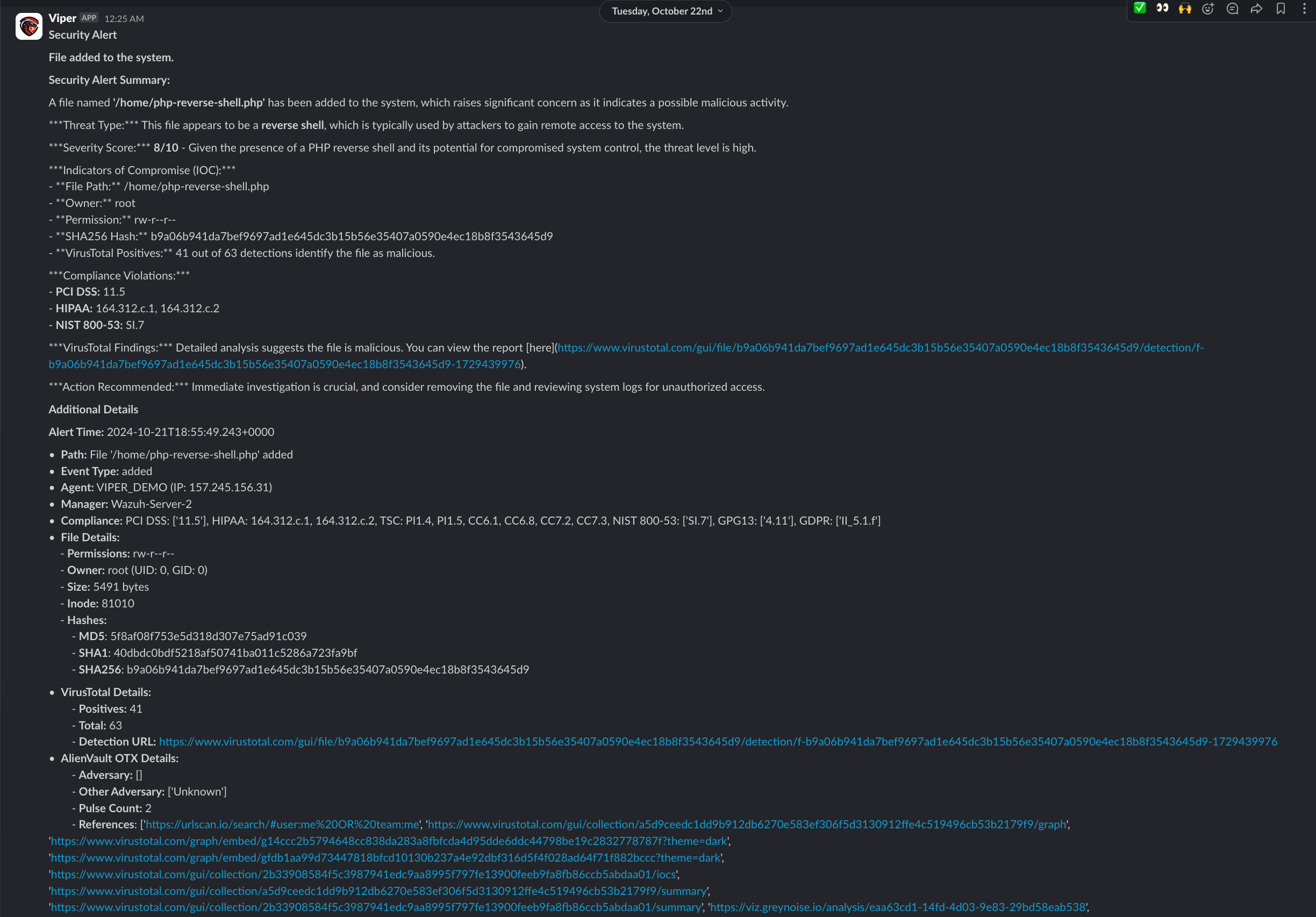
Example Slack alert,
Limitations and Future Plans
Currently, VIPER is limited to processing File Integrity Monitoring (FIM) events generated by Wazuh, specifically for rules 550, 553, and 554. Future plans include expanding its capabilities to integrate with additional external threat intelligence platforms and support a broader range of Wazuh alert types, further enhancing its utility and effectiveness in cybersecurity operations.
Implementation
Detailed implementation instructions and code can be found on the project's GitHub Repository.
🤝 Help Wanted
If you have any ideas or would like to contribute to improving the project, please feel free to open an issue on the GitHub repository. I plan to continue enhancing VIPER as time permits, and help from the community would be greatly appreciated—especially with integrating new alert types and conducting thorough testing. Your input can make a significant difference in refining and expanding the tool’s capabilities!

Member discussion